In a shocking new development, car thieves are now using fake JBL speakers to gain access to vehicles and steal them within a matter of minutes. This new tactic goes beyond the traditional methods of smashing windows or relaying FOB code sequences and instead exploits the vehicle’s controller area network (CAN).
A cybersecurity expert’s discovery
The discovery was made when a cybersecurity analyst specializing in automotive security found that his Toyota SUV had been targeted by thieves using this new technique. Ian Tabor, the cybersecurity and car hacking expert, identified CVE-2023-29389, which highlights that Toyota RAV4 vehicles can automatically trust messages from other electronic control units (ECUs).
By removing the bumper and accessing the headlight connector, thieves can tap into the CAN bus and send a forged key validation message. Once validated, the car can be started and driven away without any trouble.
Reverse engineering the emergency start device
Tabor’s investigation led him to purchase and analyze an emergency start device, which is typically used by owners or locksmiths when a key is lost or unavailable. He collaborated with another automotive security expert, Ken Tindell, to reverse engineer the device and understand its communication with the Toyota’s CAN bus.
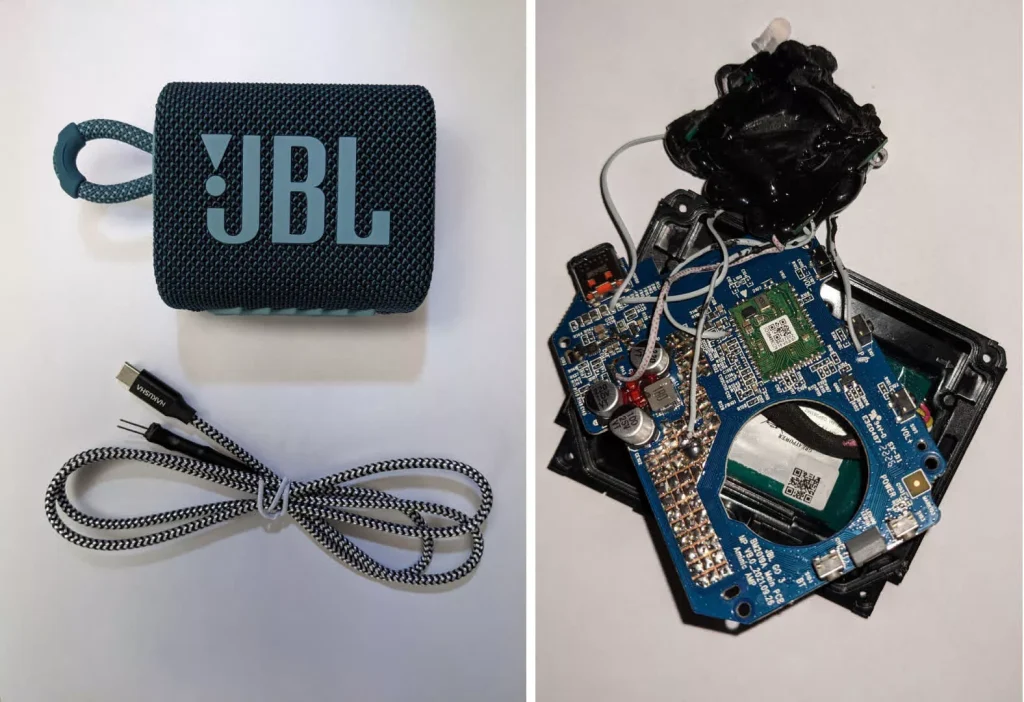
Surprisingly, the emergency start device resembled a simple JBL portable speaker. Tindell explained that a fake play button on the speaker case is wired to a PIC18F chip. Pressing the button sends a CAN message burst that instructs the door ECU to unlock the vehicle’s doors. The thieves then disconnect the CAN Injector, enter the car, and drive off.
Vulnerability in other vehicles
Although the attack was successfully replicated on a Toyota RAV4, it is reasonable to assume that similar attacks could be carried out on other vehicles with the same technology and architecture. Tabor and Tindell have informed Toyota about the vulnerability, hoping that the automaker can address the issue and prevent further exploitation. Unfortunately, they have not yet received any acknowledgement or response from the company.
For more details on the device, how it works, and how easily it can be fabricated, visit the Canis Automotive Labs website. Stay tuned to GizmoChina as we keep you updated on the latest developments in automotive security and technology.



 Shiftdelete.net
Shiftdelete.net










