The official website of Xubuntu, a popular Linux distribution, was targeted by cyberattackers during the weekend of October 18-19, 2025. Users visiting the site to download the operating system unknowingly encountered Windows-based malware. The attack specifically targeted the link used to download the distribution’s torrent file.
Users attempting to switch from Windows to Xubuntu were targeted
Users who should have normally downloaded a .torrent file instead downloaded a fake ZIP archive called xubuntu-safe-download.zip. This archive contained a Windows executable (.exe) and a “terms of service” text file. This posed a serious risk, especially for users unfamiliar with the Linux world.
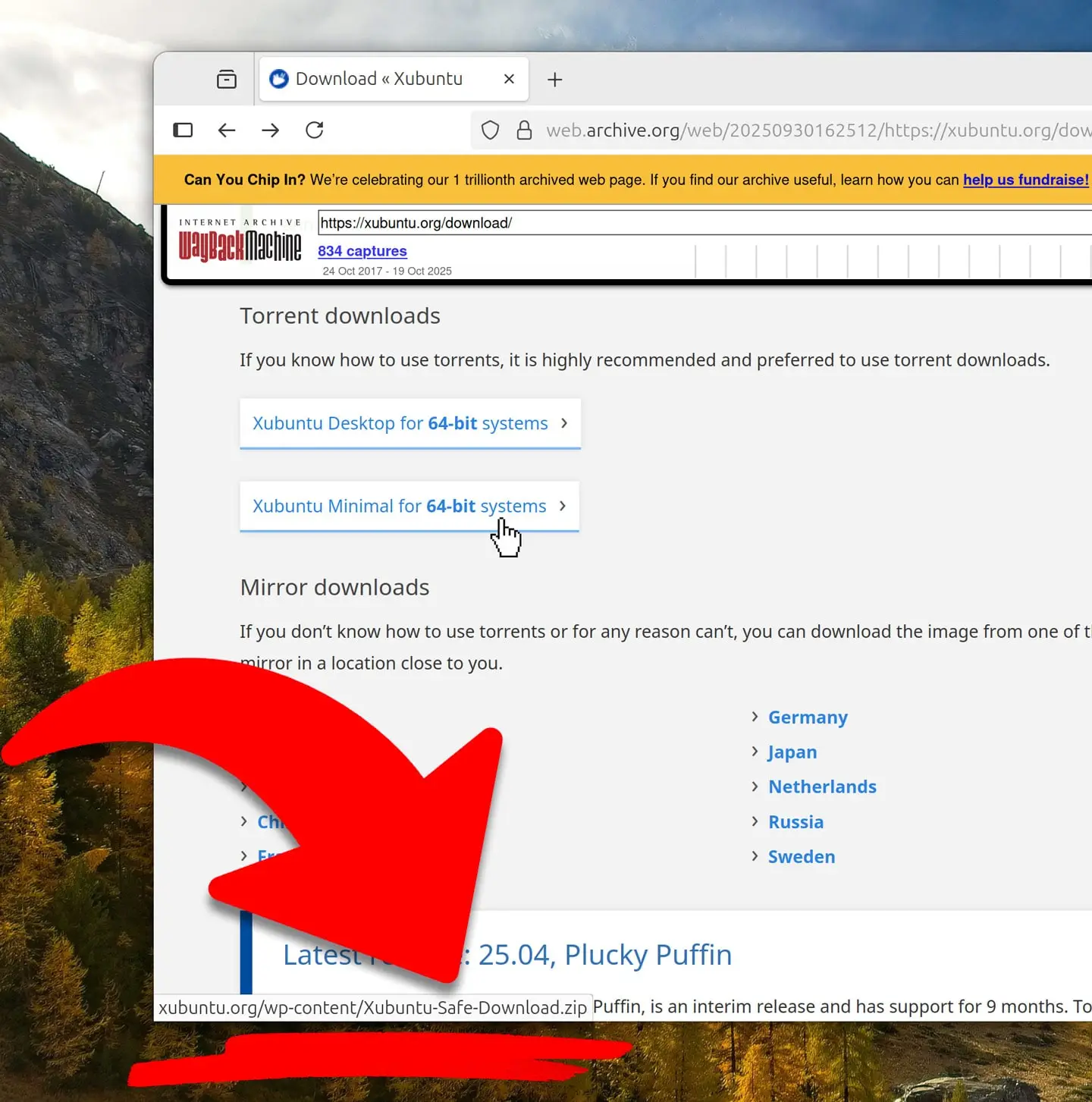
Investigation revealed that the .exe file inside the fake ZIP file was malware. Its primary purpose was to obtain sensitive information, such as cryptocurrency wallet addresses, that users copied to the clipboard. It’s believed that the attackers may have targeted less technically savvy Windows users, taking advantage of the increased interest in Linux distributions following the end of Windows 10 support.
The Xubuntu team immediately removed the affected download page upon being notified. Team leader Sean Davies stated in a statement that they would accelerate the transition from their old WordPress infrastructure to a more secure static site. It was also emphasized that this attack only affected the torrent link on the Xubuntu website, and that ISO downloads or the infrastructure for other Ubuntu versions are secure.
Such vulnerabilities once again demonstrate the importance of using only official and trusted sources when downloading software. The Xubuntu team recommends that users use the official Ubuntu CD image server for downloads until the issue is fully resolved. What are your thoughts on this incident? Have you ever encountered a similar security issue?