AMD has announced a new security vulnerability named Sinkclose, which could potentially affect millions of Ryzen and EPYC processors worldwide. This vulnerability, recorded under the code “CVE-2023-31315,” allows attackers to execute malicious code within the system’s most sensitive area, the “System Management Mode” (SMM). So, how can this be prevented?
AMD Takes Action on High-Risk Sinkclose Security Vulnerability: Millions of Ryzen and EPYC Processors Affected
This situation raises serious security concerns, as an attack executed within the SMM could lead to undetectable malware, like bootkits, bypassing antivirus software. But what exactly is Sinkclose?
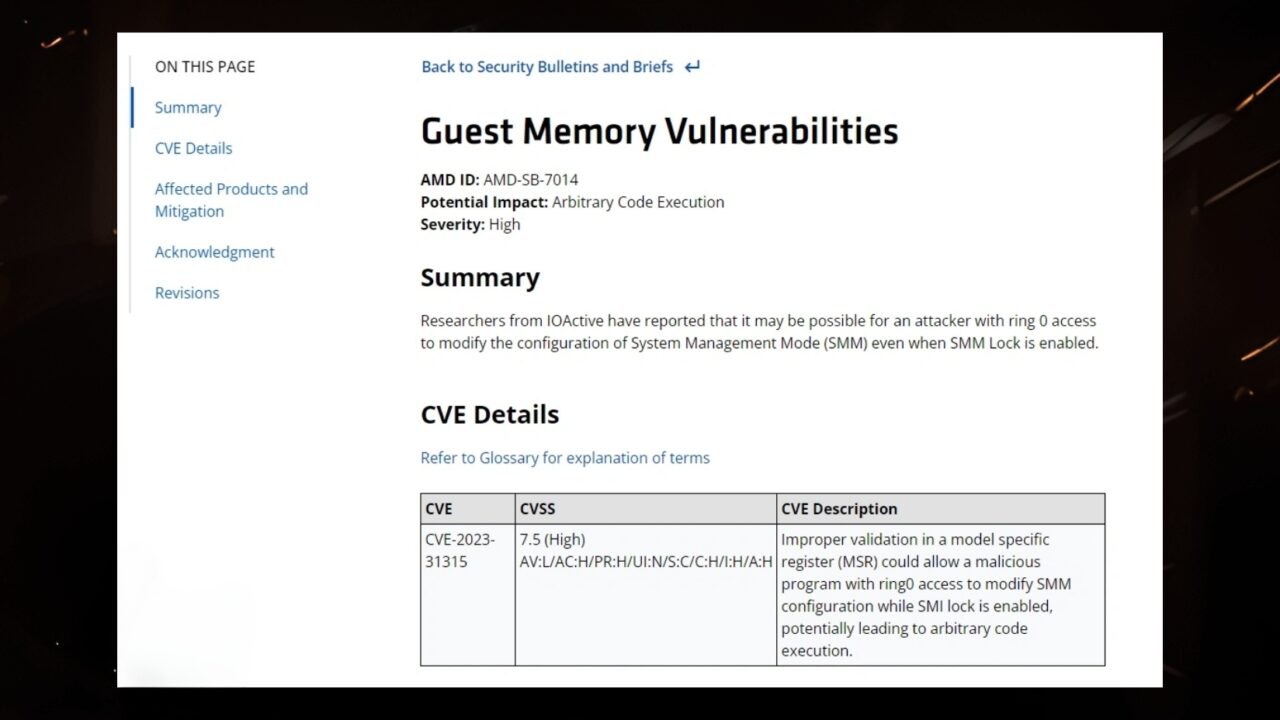
Sinkclose is a security vulnerability that arises specifically within the System Management Mode (SMM), a special operational mode designed for processors. SMM is intended for advanced power management and operating system-independent functions and can only be accessed through a System Management Interrupt (SMI).
This mode operates independently of traditional CPU functions and is critical for overall system security. However, the Sinkclose vulnerability allows attackers to infiltrate the SMM and execute malicious code. So, which processors are affected?

According to AMD’s security bulletin, this vulnerability affects many newer processors, including the Ryzen 3000 series and the first-generation EPYC processors. These vulnerable CPUs have reached millions of users worldwide.
AMD has begun to release new firmware and microcode updates to mitigate the effects of this vulnerability. However, a fix for Ryzen 3000 series desktop processors has not yet been planned, posing a significant security risk for users of this series. So, what should be done for protection?
Steps to Mitigate the Sinkclose Vulnerability
AMD has released firmware and microcode updates for affected processors to mitigate the Sinkclose vulnerability. These updates are designed to make it more difficult for attackers to access the SMM, thereby preventing such attacks. AMD strongly recommends that users install these updates as soon as possible.
For enterprise-level systems using EPYC processors, these updates are crucial for maintaining system security. Users should regularly check and apply updates to their system management software and BIOS to protect against such security vulnerabilities.
Similar risks exist for AMD Ryzen 3000 series processors as well. For individual users, not being aware of this security vulnerability could leave their systems defenseless. Therefore, it is essential for users to not neglect these updates and to regularly check their systems.
What are your thoughts on this security vulnerability? Do you think AMD’s measures are sufficient? Feel free to share your views in the comments below.














