Cybercriminals are increasingly turning to legitimate commercial packer apps like BoxedApp to evade detection, according to Jiří Vinopal, a threat researcher at Check Point Research. Over the past year, the abuse of BoxedApp has surged, with remote access trojans (RATs) like Agent Tesla, AsyncRAT, and QuasarRat, as well as ransomware strains such as LockBit, exploiting its capabilities to slip past static analysis.
BoxedApp, known for its robust features, has been co-opted by malware developers to create virtual processes that bypass traditional endpoint protection systems. “The virtual processes may make it harder for anti-malware tools to detect the malware running via the BoxedApp SDK,” explained application security expert Sean Wright. This method of evasion has resulted in a higher false positive rate for BoxedApp-packed applications, complicating the task for security teams.
Most malicious submissions originating from Turkey, the US, and Germany
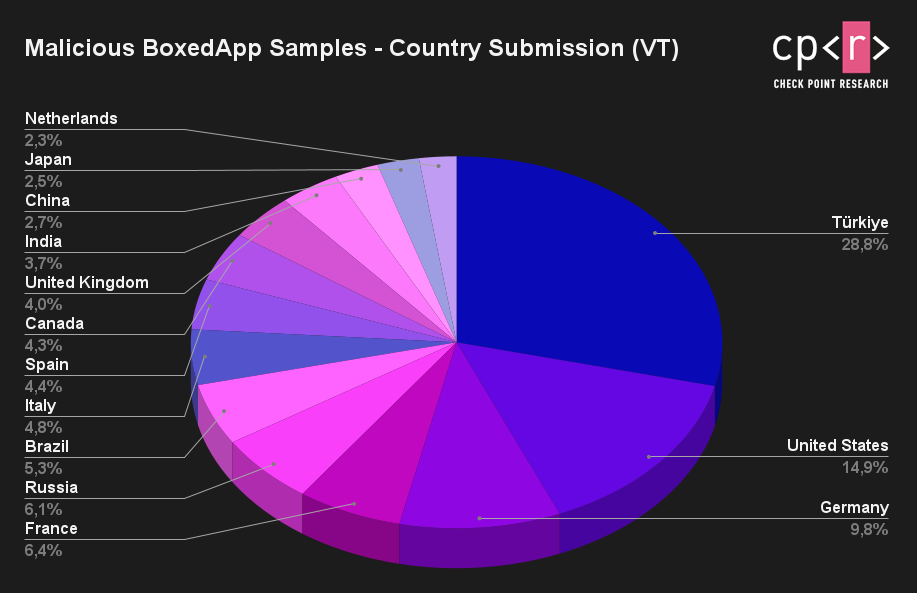
Check Point Research’s analysis of VirusTotal submissions revealed that 25 percent of BoxedApp-packed malware samples were flagged, with most malicious submissions originating from Turkey, the US, and Germany. These attacks predominantly targeted financial institutions and government sectors.
Security experts advise organizations to limit the use of BoxedApp and employ controls such as application signing to mitigate the risks associated with its abuse. For more detailed detection, Check Point Research offers Yara signatures to identify and analyze packed applications.
For more details and insights, refer to the full report by Check Point Research.














