Windows 10 and 11 operating systems are facing a new security threat known as RID Hacking. The Relative Identifier (RID) system serves as a unique identifier that determines a user’s access level. Through attacks targeting this system, a low-privilege user account can potentially be elevated to an administrator account. So, what measures can be taken to protect against this threat? Details are in our report…
Administrator Privileges Gained Through RID Hacking on Windows 10 and 11
To begin with, RID in Windows is a unique identifier assigned to every user. For instance, the RID value of an administrator account might be “500,” while that of a regular user could be “1000.” RID Hacking involves altering this value to escalate the privileges of an account. However, for this attack to occur, the attacker first needs to gain SYSTEM-level access to the system. Here’s the typical process an attacker follows:
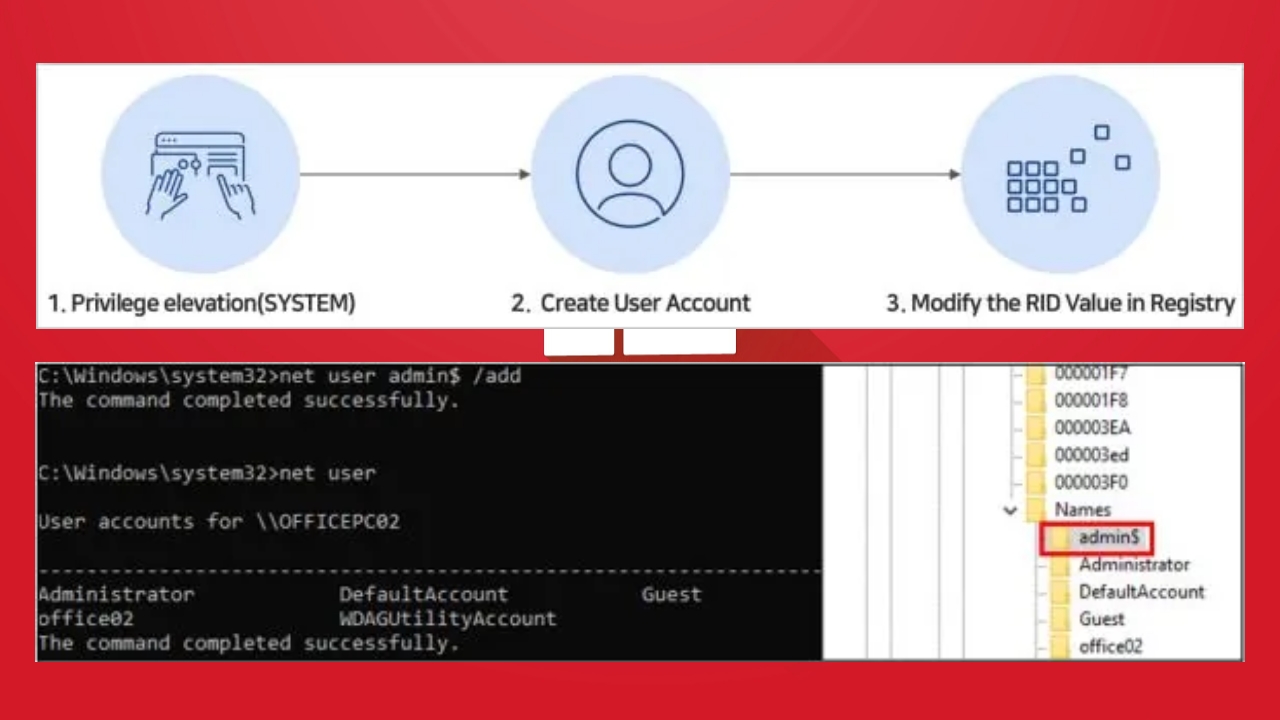
- SYSTEM access is obtained: The attacker exploits security vulnerabilities to gain SYSTEM-level access.
- A hidden account is created: Using the “net user” command, a low-privilege account is created, visible only in the SAM (Security Account Manager) registry.
- RID is modified: The attacker changes the RID value of this account to match that of an administrator account, effectively escalating its privileges.
- Remote access is enabled: The attacker adds the new account to the remote desktop users and administrator groups.
- Traces are erased: The attacker modifies registry data and clears system logs to hide their tracks.
How Can This Threat Be Prevented?
To protect against attacks like RID Hacking, the following measures can be taken:
- Restrict access to the SAM registry: Prevent unauthorized users from accessing this sensitive area.
- Use multi-factor authentication: Add an extra layer of security for all accounts.
- Block the use of suspicious tools: Limit the execution of tools commonly used in attacks, such as PsExec and JuicyPotato.
- Disable guest accounts: Guest accounts, which are often enabled by default, pose security risks.
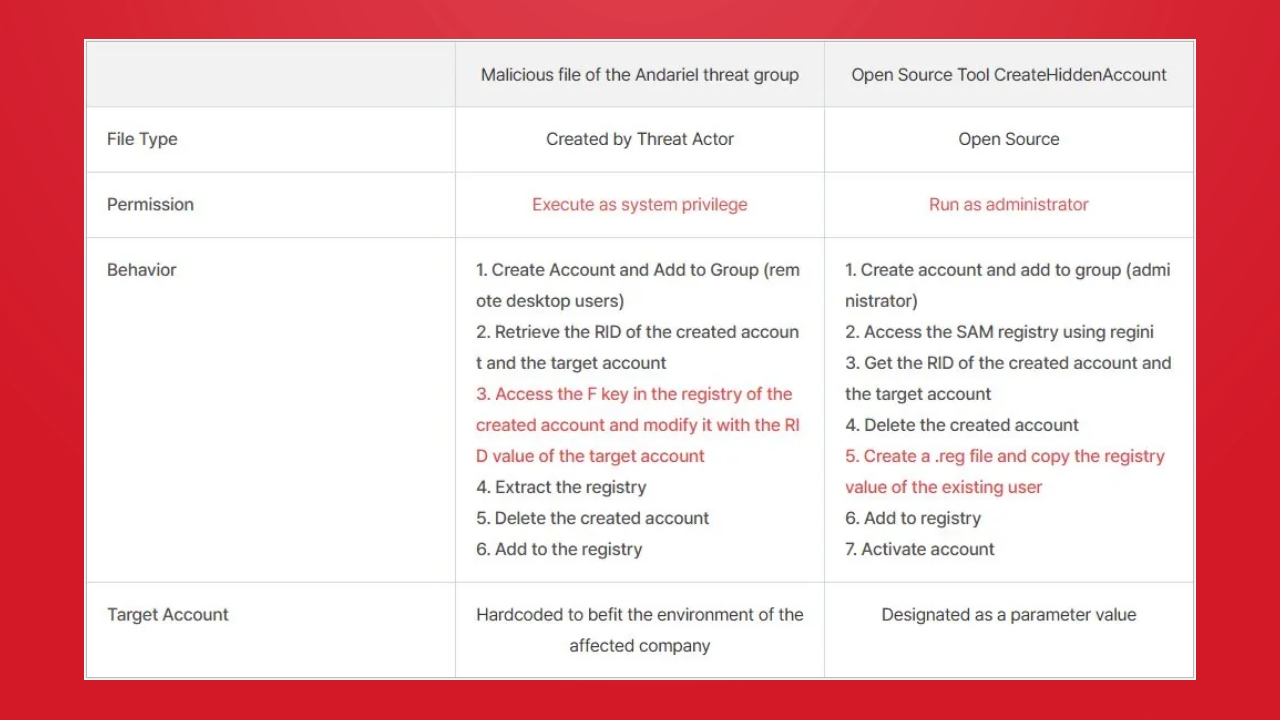
Experts warn that RID Hacking is a dangerous method because it is very difficult for users to detect such attacks. Once SYSTEM access is obtained, the attacker’s actions can persist even after the system is rebooted, leaving no trace.
What do you think about this threat? What measures are you taking to protect your systems? Share your thoughts in the comments below!














