Malicious software targeting personal data, especially in banking, is becoming even more frightening with new versions. The XLoader Android malware, first detected in previous years, now with its new version, behaves like Google Chrome to access user data. Here are the details…
XLoader Android malware returns with a new version
A new version of the malicious software XLoader (also known as MoqHao) has been discovered. Previously, this malware was detected in many countries, including the United States, United Kingdom, Germany, France, Japan, South Korea, and Taiwan.
The malware spreads through SMS text messages containing a shortened URL link. Additionally, XLoader becomes active immediately after installation. It’s worth noting that this allows the malware to operate in the background without being detected while stealing personal data.
McAfee, commenting on the malware, stated, “Malicious activities start automatically upon application installation. We have already reported this technique to Google, and they are already working on implementing mitigating measures to prevent such automatic execution in future Android versions.”
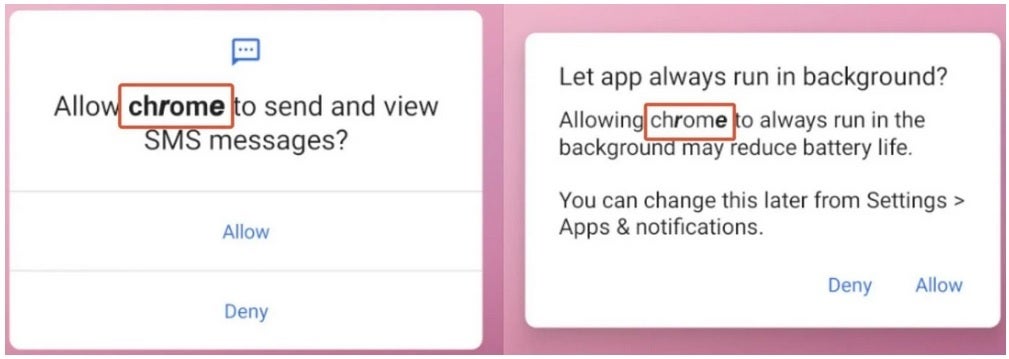
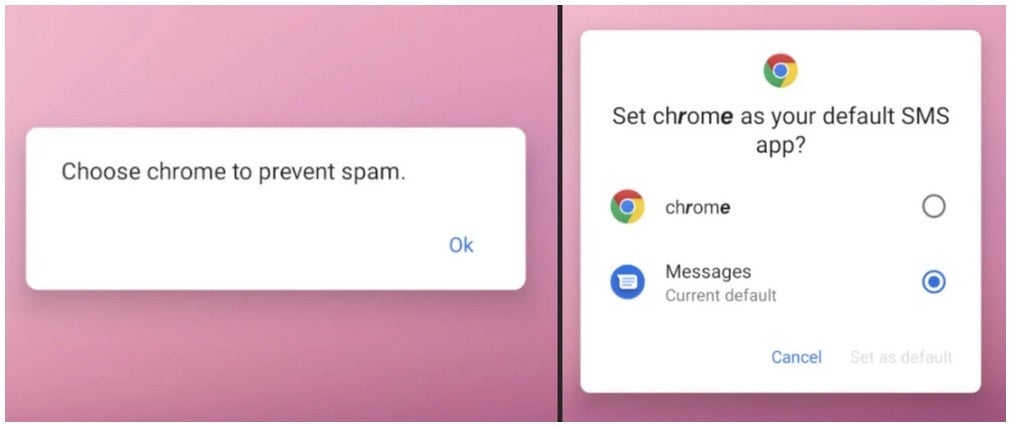
The XLoader software behaves as if it is coming from Google Chrome, requesting permission to send and view SMS (text) messages and to allow the fake Chrome to run in the background. It also requests permission to set the fake Chrome as your default SMS application, thereby accessing users’ SMS details.
McAfee emphasized that the new XLoader malware is much more dangerous than the previous one due to requiring minimal interaction from the victim. Security researchers advise against clicking on shortened links, even if they come from familiar contacts.














