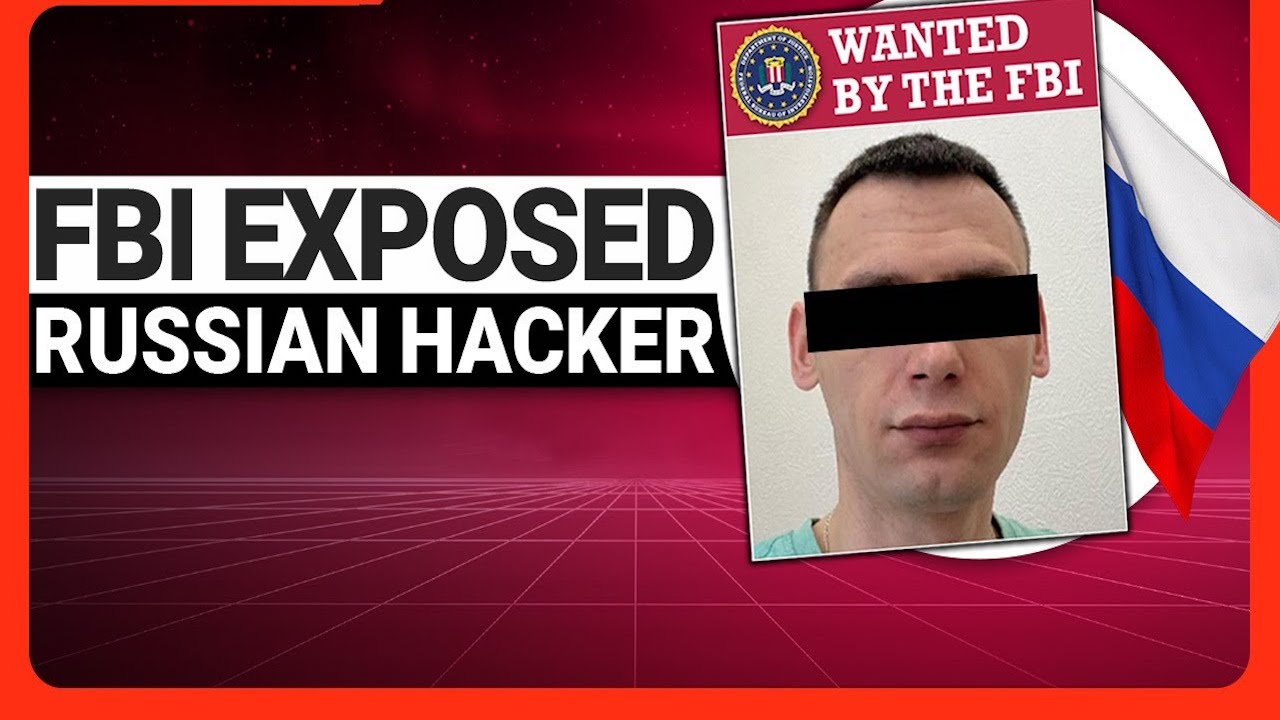
A significant development in the global fight against ransomware took place as the U.S. Department of Justice (DoJ) announced charges against Ruslan Magomedovich Astamirov, a Russian citizen. Allegedly, Astamirov was instrumental in launching the notorious LockBit ransomware across the U.S., Asia, Europe, and Africa.
Crimes Unveiled
Astamirov, a 20-year-old from the Chechen Republic, reportedly executed at least five cyberattacks from August 2020 to March 2023. His capture occurred last month in Arizona. The DoJ detailed that Astamirov purportedly conspired with other LockBit associates, committing wire fraud, intentionally damaging computers, and demanding ransoms through ransomware deployment.
In his LockBit endeavors, Astamirov operated various email addresses, IP addresses, and online accounts to dispatch the ransomware and negotiate with victims. Some of the ransom payment from an unnamed victim was traced back to a virtual currency address under Astamirov’s control.
Consequences await
If found guilty, Astamirov could face a prison sentence of up to 20 years for the first charge and a maximum of five years for the second. The case against Astamirov is the third LockBit-related prosecution in the U.S., following Mikhail Vasiliev, currently awaiting U.S. extradition, and Mikhail Pavlovich Matveev, indicted last month in connection with LockBit, Babuk, and Hive ransomware attacks.
Notorious co-conspirators
Matveev remains elusive. In a conversation with The Record, Matveev conveyed his lack of surprise at being included in the FBI‘s Cyber Most Wanted list. The self-taught hacker claimed the attention on him would soon fade and expressed his ambition to elevate Russia’s IT sector.
Ransomware warnings
The DoJ’s announcement arrived concurrently with a joint warning about LockBit ransomware. This cautionary advice originated from cybersecurity authorities in Australia, Canada, France, Germany, New Zealand, the U.K., and the U.S.

The operation of LockBit follows the ransomware-as-a-service (RaaS) model. The primary team enlists affiliates to conduct attacks on corporate networks, offering them a share of the illegal profits.
In a method known as double extortion, the affiliates first encrypt the victim’s data and extract it. They then resort to threats of revealing this stolen data on leak sites, putting pressure on victims to pay ransoms.
Since late 2019, the group has initiated nearly 1,700 attacks. However, the actual figure may be higher as the dark web data leak site only discloses victims who refuse to pay ransoms.
We invite our valued readers to share their views on this issue. What are your thoughts on these developments in global cybersecurity? Please share your insights in the comments section below!