Def Con 2023, one of the world’s largest computer hacking conferences, hosted some highly intriguing scenes. During the conference, participants were shown how a cheap device could potentially expose sensitive user data. Additionally, this device is capable of mimicking Apple notifications. Here are the details!
The $70 device is a combination of various products!
Participants of the hacking conference Def Con are accustomed to witnessing odd scenes, like revealing people’s passwords. However, this year’s event featured something quite astonishing. Security researcher Jae Bochs demonstrated in a research project how exploiting Apple’s own Bluetooth Low Energy (BLE) usage can make it remarkably easy to compromise a user’s information.
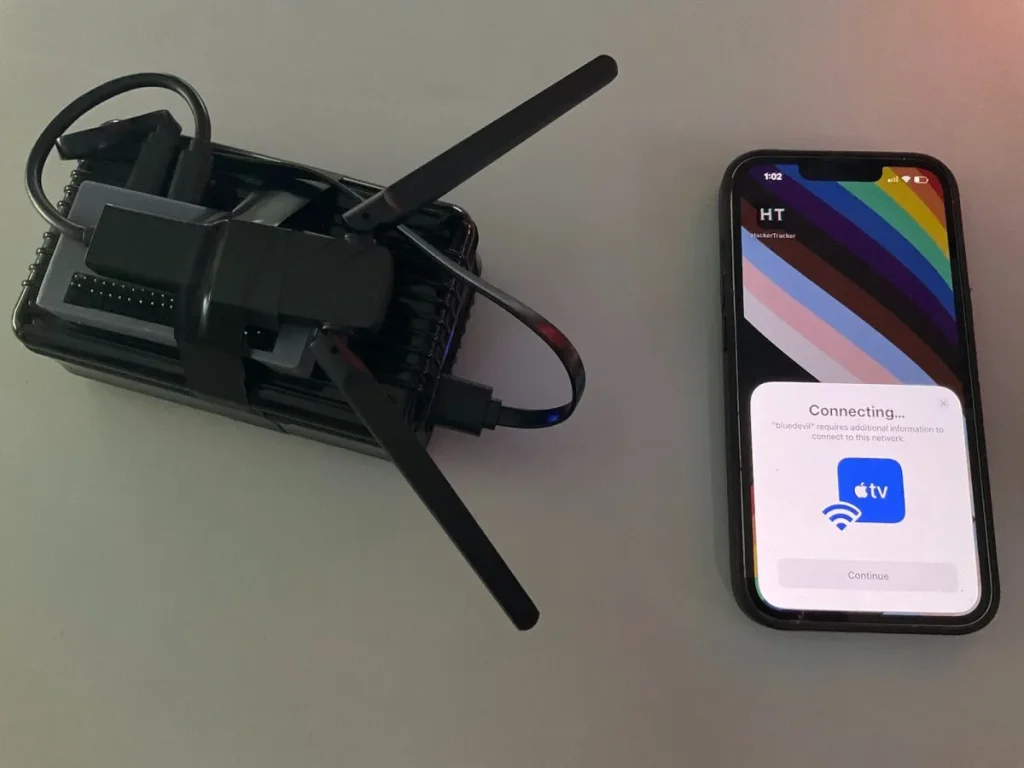
Bochs had two objectives with this project. The first was to demonstrate to people that simply turning off Bluetooth through the Control Center isn’t sufficient to disable it. The second was to have fun. For this project, Bochs utilized a device consisting of a Raspberry Pi Zero 2 W, a Linux-compatible Bluetooth adapter, several antennas, and an external battery.
Moreover, this device is said to cost around $70. Within the scope of the project, it was revealed that Apple’s Bluetooth Low Energy (BLE) protocols allow communication between the company’s devices. Additionally, Bochs noted that Apple devices focus on “proximity actions” on the iPhone screen when they come close to each other.
During the conference, the security researcher was able to send a message to nearby iPhones, prompting them to automatically fill in their passwords to an Apple TV, even when there was no Apple TV present in the vicinity. Bochs didn’t design this device to obtain any personal information. However, the possibility of this happening seems quite high. In summary, a $70 device can mimic iPhone notifications and deceive individuals.
So, what are your thoughts on Apple imitation? Don’t forget to share your opinions with us in the comments section!














