This time, the new malware Atomic macOS Stealer, which targets Mac users, is on the agenda. It is necessary to be careful against malware that can steal a lot of data. Malware is of course not only prepared for the Windows operating system. Different malware options continue to come to the agenda for Apple-signed computer models with the macOS operating system.
Atomic malware can steal Keychain info, files, crypto wallets, etc…
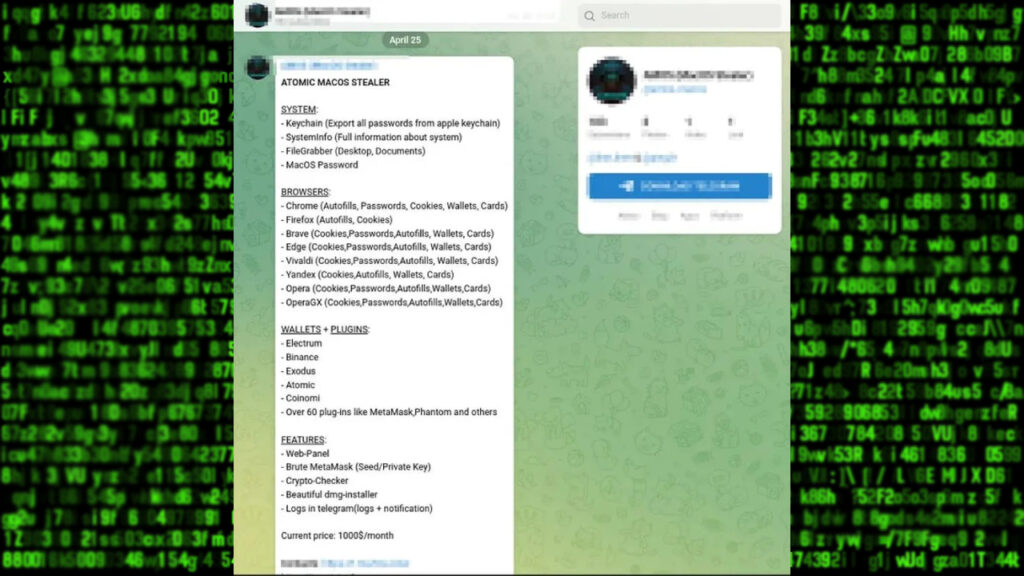
The newest of these, Atomic macOS Stealer malware, is sold by a person over Telegram with a monthly usage fee of $ 1,000. Atomic is sent to systems as a DMG file. If installed, it asks people for the system password through a fake window. If this password is given, Atomic can steal iCloud KeyChain passwords, cookies, passwords (they can capture all automatically logged-in pages), and credit card information from Chrome, Firefox, Brave, Edge, Opera, and more. Atomic, which is very dangerous, can also compromise crypto wallets such as Binance, Exodus, Electrum, and MetaMask.
In order to protect against this and similar malware, it is necessary not to install applications on Mac computers from outside the App Store or from anywhere of unknown origin. At the same time, you should keep the device’s systems constantly updated, not give unnecessary access permissions to applications, and avoid suspicious links sent via e-mail.
You should also beware of “MacStealer” malware too
Similar to this, another malware that came to the agenda before was MacStealer. MacStealer, which focuses directly on information theft, can steal credentials, cryptocurrency wallets, and some other sensitive files stored in web browsers, especially password/login information in iCloud KeyChain (Apple’s built-in password manager). MacStealer can also collect passwords, cookies, and credit card data saved in Firefox, Google Chrome, and Brave browsers.

It can run on macOS Catalina and higher operating systems. It can silently perform theft on Mac computer models with Intel or M-Series processors too. This malware is currently distributed mainly through the “Weed.dmg” application file. When this “dmg” file is opened, the malware opens a fake password prompt that appears to come from the system. When you enter the system password here, all data that can be obtained from the computer is collected together. These data are converted into a .zip file and transferred to the other side over the internet. To cover its tracks, MacStealer automatically deletes the stolen data.













