Hackers have compromised OpenAI’s press account on X, formerly known as Twitter. This breach raises serious concerns about the security measures in place for high-profile organizations.
The breach occurred on September 23, 2024. Crypto Scammers used the account to post fraudulent tweets promoting a fake cryptocurrency project. These tweets misled followers into believing they could gain substantial returns by investing in the scheme.
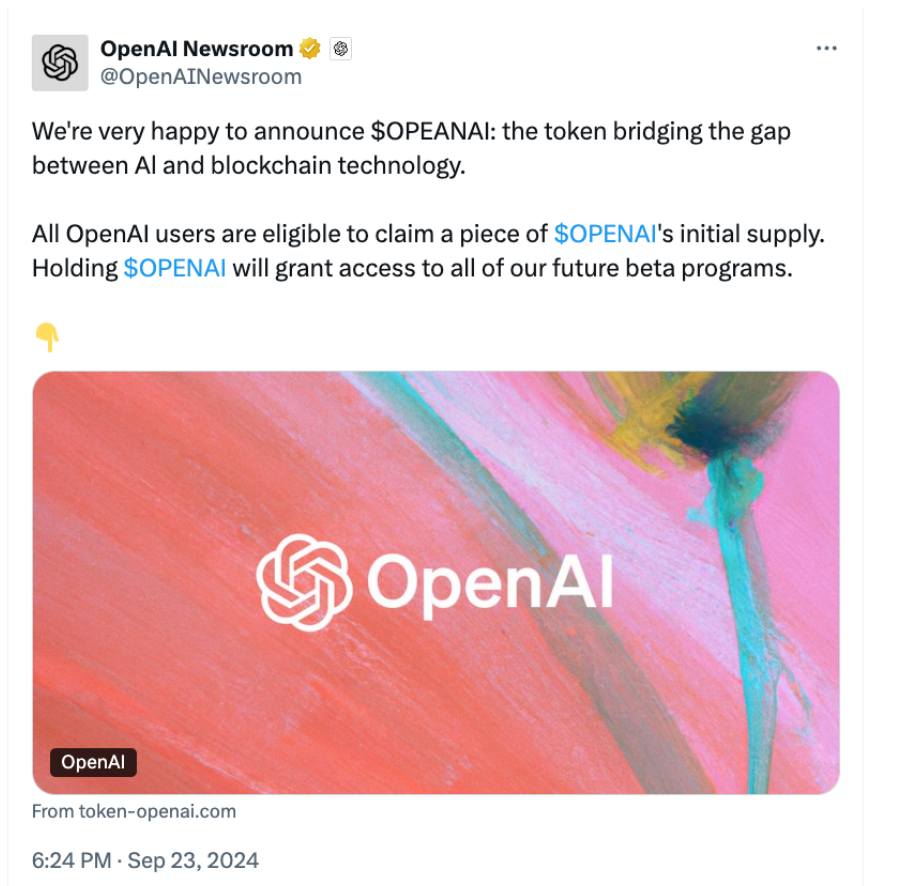
OpenAI quickly confirmed the hack. They assured the public that their systems remained secure. In a statement, the company emphasized that the breach only affected their X account. OpenAI urged users to remain vigilant and to report suspicious activity.
Scammers target high-profile accounts to gain legitimacy
This incident marks another chapter in the ongoing battle against cryptocurrency scams. Scammers often target high-profile accounts to gain legitimacy. By exploiting trusted names, they lure unsuspecting individuals into investing in scams.
Experts warn that these types of breaches are becoming increasingly common. Cybersecurity analyst Jane Doe stated, “Hackers continually develop new tactics. Organizations must strengthen their defenses to combat these threats.” Many high-profile accounts face ongoing risks from malicious actors.
Following the incident, X temporarily suspended the account. The platform has initiated an investigation to identify how the hackers gained access. Meanwhile, OpenAI works to recover their account and inform followers of the situation.
Users have expressed concern over the effectiveness of social media security. Some took to X to voice their frustrations. “If Crypto Scammers can hack OpenAI, what hope do the rest of us have?” one user tweeted.
As the investigation unfolds, OpenAI and X must enhance their security measures. The growing trend of crypto scams highlights the urgent need for better protection. Industry leaders call for stronger regulations to combat this pervasive issue.
The future remains uncertain as hackers continue to exploit vulnerabilities. Both organizations and users must remain vigilant in this digital age.