Serious security vulnerabilities have been discovered in the digital recruiting platform McHire, used by the vast majority of McDonald’s branches. Developed by Paradox.ai, the system uses a bot named Olivia to automatically receive job applications and chat with candidates. This system, which collects personal information from candidates, has exposed the data of millions of people due to weak security measures.
A significant security vulnerability has been discovered in McHire.
Some user complaints initially surfaced on Reddit that the bot was providing meaningless answers. A brief security review revealed that the system’s admin panel was accessible with the username and password “123456.”
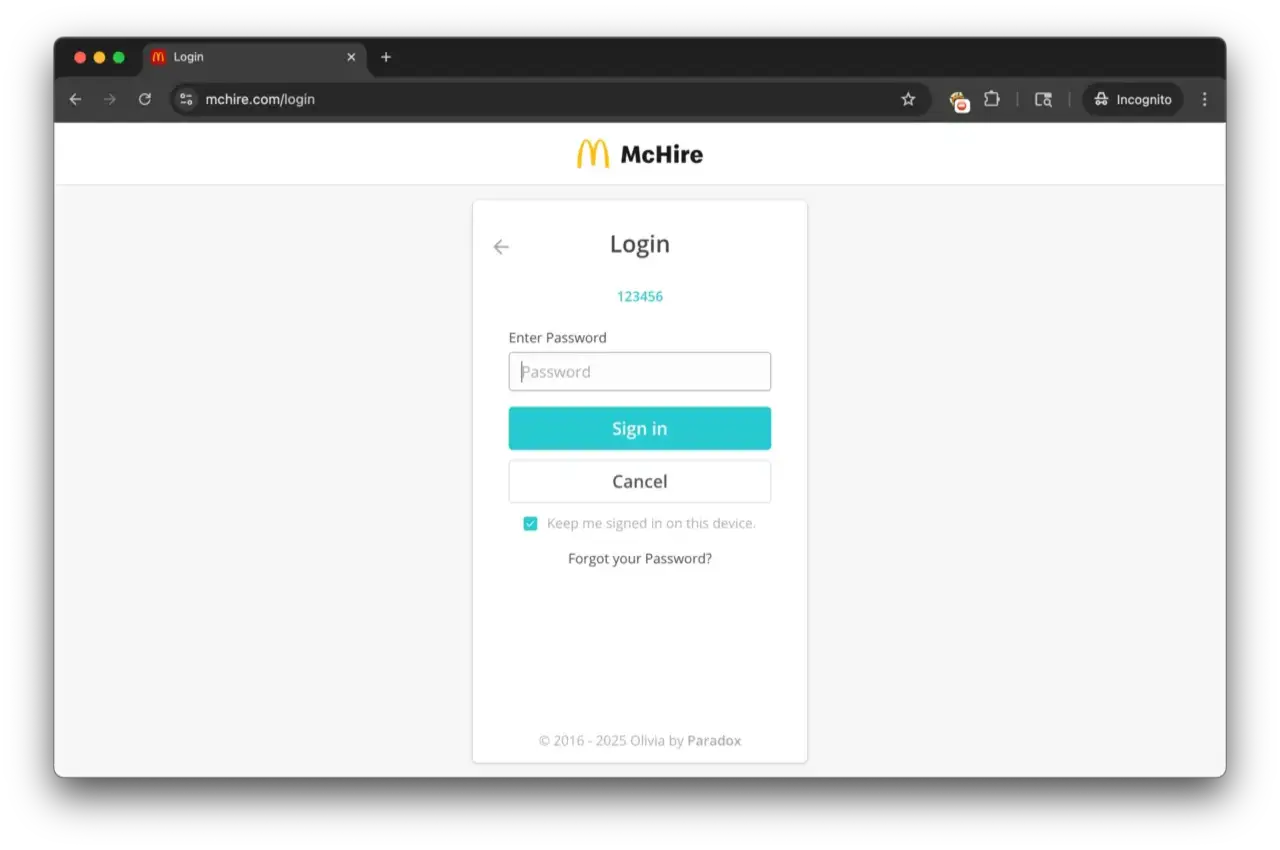
Once logged in, full access was granted to an administrator account created for the test restaurant owned by Paradox.ai. This allowed for a detailed examination of both the recruiting process and the platform’s functionality.
During the application process, candidates enter information such as their email address, phone number, and shift preferences into the system through the bot named Olivia. They are then directed to a personality test. In this test, responses like “likes to work overtime” are required, either “applies to me” or “doesn’t apply.”
After the test is completed, the system pauses and awaits human confirmation. The review team made some attempts to modify the bot’s responses, but the system was configured to accept only predefined responses.
The true extent of the security vulnerability was revealed in the API queries used during the application process. In an API call processing candidate data, it was discovered that simply changing the application number (lead_id) allowed access to applications from other candidates in the system.
When the number was manually reduced, personal information belonging to different individuals began to appear directly in the API response. This system, which lacked any authentication mechanism, made it possible to access millions of applications submitted to McHire.
Data obtained through the API includes name, email address, phone number, address, all forms filled out by the candidate, a record of their preferences, and information about the application’s progress.
The system also directly shared session tokens that allowed candidates to log in to the user interface. This gave them access to their past conversations and personal records within the system.
Paradox.ai confirmed the vulnerability, disabled the relevant API access, and initiated system-wide security scans to identify other potential vulnerabilities. The company announced that it has tightened its security measures, emphasizing that protecting candidates’ and customers’ data is its top priority.













